Anybody remember the classic Beachboys song ‘Surfing USA’? Well how about ‘Surfing LNER’ as an alternative?
I am getting dismayed in my classes as my references to all time great music hits are now being met with sideways glances and silence from an audience of cyber students who are mostly in their early 20’s and have no idea what I am talking about.
I often quote lyrics from the Beachboys, Queen, Meatloaf, the Beatles and Tom Jones in my well-crafted anecdotes and witty remarks but normally have to explain the joke afterwards! Which kind of loses the point. However, if there are any dads out there – you will know that our jokes are the funniest on the planet, even if nobody laughs.
It makes me feel old but it don’t stop me now as I’m having a good time.
Luckily I removed Gary Glitter and Rolf Harris from my repertoire some time ago.
I remember when I first ventured into the world of IT security many years ago (well before the time that we slapped the word ‘cyber’ in front of everything) and being taught about all of the different types of attacks ranging from application attacks, network intrusions, man in the middle and then something lovingly referred to as social engineering.
Little did I know that I had been involved in the majority of these activities for over 20 years in my previous life in the military – but now I could put a label on it all!
I really enjoy talking about and training people on the concepts of social engineering and could probably write a book on it – or perhaps compose a musical comedy which would have more impact ‘The Pen-testers of Penzance’?!
What I really enjoy is putting together courses which decipher all the jargon of social engineering – and the really great thing is that a lot of these terms are now common knowledge:
- Phishing
- Spear-phishing
- Whaling
- Smishing
- Vishing
The list is pretty endless.
Then we get into the world of ‘physical’ social engineering which takes a certain element of tradecraft and bravado to pull off:
- Piggy-backing
- Tailgating
- Impersonation
- Dumpster diving
- Shoulder surfing
All relatively easy concepts to understand as they pretty much do what they say on the tin.
Shoulder surfing is a good one as it is often explained as someone looking over your shoulder to see what you are up to on a screen or how your hands move on a keyboard whilst typing in credentials etc. And you may think – “How likely is that to take place whilst I am at work?”. The reality is of course that unless the attacker has been able to get physical access to where you are sitting (through tailgating or piggy-backing perhaps?) – then it is not likely at all. (Unless you work with a bunch of ‘disgruntled employees’!)
However, don’t know if you have noticed recently that things have changed?
Technology now means that each and every one of us is equipped and has the ability to record, photograph and video at the drop of hat – whoever, whatever, whenever. That is what a mobile phone is for. More camera less phone.
Life now means that more and more of us are working away from the office and we are all busy people.
We work routinely from home, check our emails on the toilet, we answer calls in the coffee shop, we arrange video meetings on the move which unfortunately means that the social engineer no longer needs to come to us as we come to them!
On a recent trip up North (where it wasn’t at all grim) I was sat on a London North East Railway train doing what most people do on trains. Reading a book, listening to music and playing with my phone. Nobody raised an eyebrow at any of this. However, two seats in front of me was a very busy person working on that all important Teams meeting and although she wasn’t talking she was typing. This was the view from my seat.
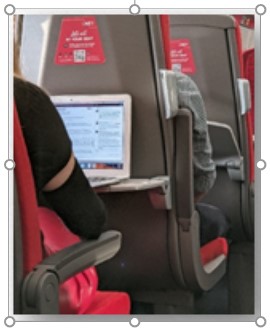
Look carefully, you can see her shoulder.
I don’t have a particularly ‘smart’ smart phone but it does allow me to zoom in nicely with the camera and video recorder. And so, from two seats away, hidden in plain sight – I am shoulder surfing like a pro.
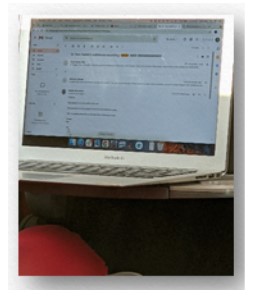
- Personal chat
- Contacts
- Personal Identifiable Information
- Company confidential information
- Email addresses
- Email login and content
- Customer contacts and information
(Naturally, for ethical reasons I have blurred the screen but trust me when I tell you that I could read it very clearly)
All whilst listening to the Beachboys greatest hits. Surfing LNER.
This is not the first time I have observed this type of activity and it probably won’t be the last. Possibly the best/worst case I have seen was when a chap I was sitting next to on a flight to France, opened up his laptop and started working on a spreadsheet shortly after take-off. That time it was PII, financial records, emails, phone numbers, business records and a whole host of other stuff which I am certain I wasn’t supposed to be privy to.
To quote the great Tom Jones – ‘It’s not unusual’ to see this type of activity everywhere – as we are busy people. We need to do things when we are out and about – and I totally get it.
But we also need to be aware and ‘street smart’.
Even if it isn’t Evil-Dude the hacker who is looking over your shoulder it might be someone who has a vested interest in what you are doing or saying. Or becomes interested based on what they can see.
Personal data is personal, company confidential data is confidential, data protection is all about protecting data – it is all quite a simple concept really – and remember it is not just you that you are protecting.
Think about your working practices. Think about the working practices of your staff and members of your team. Have a chat about data protection and what data can be accessed on mobile devices. Have a chat about how secure that data is whilst it is safely encrypted at rest and in transit when using the VPN.
Have a chat about how insecure that data is whilst it’s being used for all to see.
After the chat – draw up a specific security policy or amend your existing ones. Then turn the chat into a user training and awareness session so nobody misses out on the message.
You could always boost your training sessions with some Beachboys music playing in the background (optional).